Welcome to Cloud Backup
In this article, we'll show you the steps you need to take to protect your data with Cloud Backup.
Managing Cloud Backup
With Cloud Backup, you can back up and restore data from your cloud infrastructure, such as vServers/VPS, cloud servers, and dedicated servers, as well as from your mobile devices, such as smartphones and tablets. Additionally, you can use the Cloud Backup to secure your Windows and Mac computers against malware threats, including cryptomining malware. With regular scans, Cloud Backup checks whether your computer has been infected by a virus and stops suspicious processes. To do so, it uses a continuously updated malware database and detects yet unknown malware using AI-based behavioral detection. Even ransomware gets blocked by Cloud Backup before it can lock your data by using advanced entropy analysis.
You can also use the Vulnerability Assessment module to regularly scan your computers and virtual machines for vulnerabilities so you can address them early.
Additionally, Cloud Backup offers paid add-ons that include such features as URL filtering, patch management, and forensic backups. Furthermore, with the purchase of these extensions, you can also perform the following backups, for example:
- Microsoft SQL Server and Microsoft Exchange Cluster
- Oracle Database
- SAP HANA
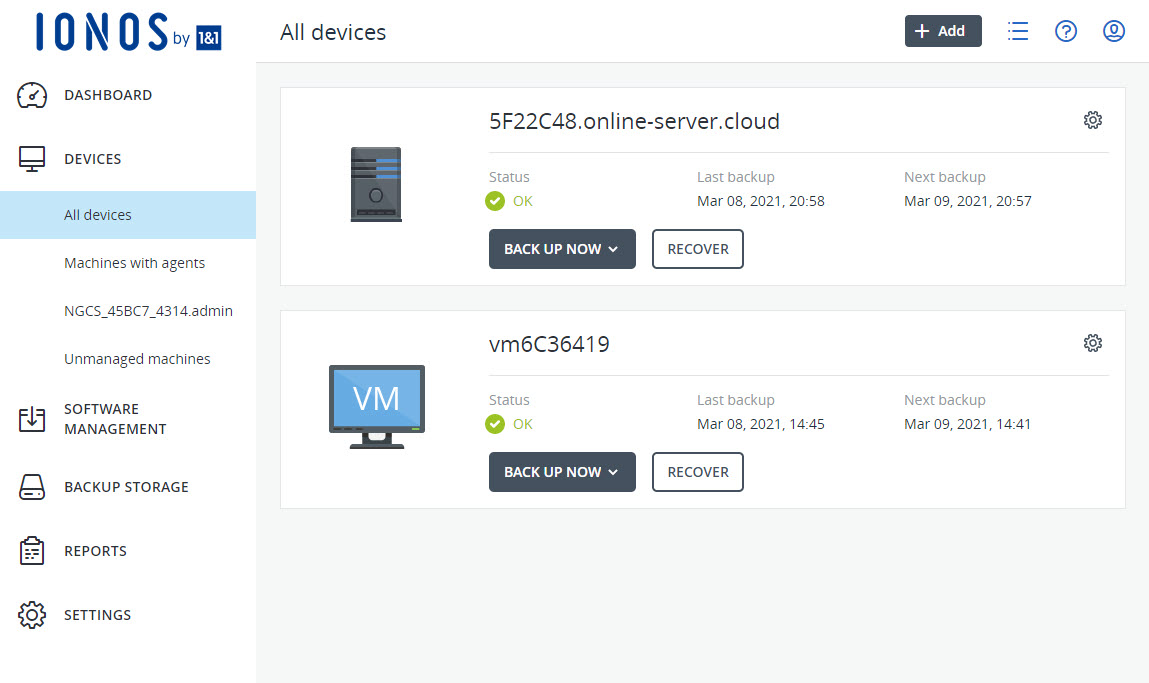
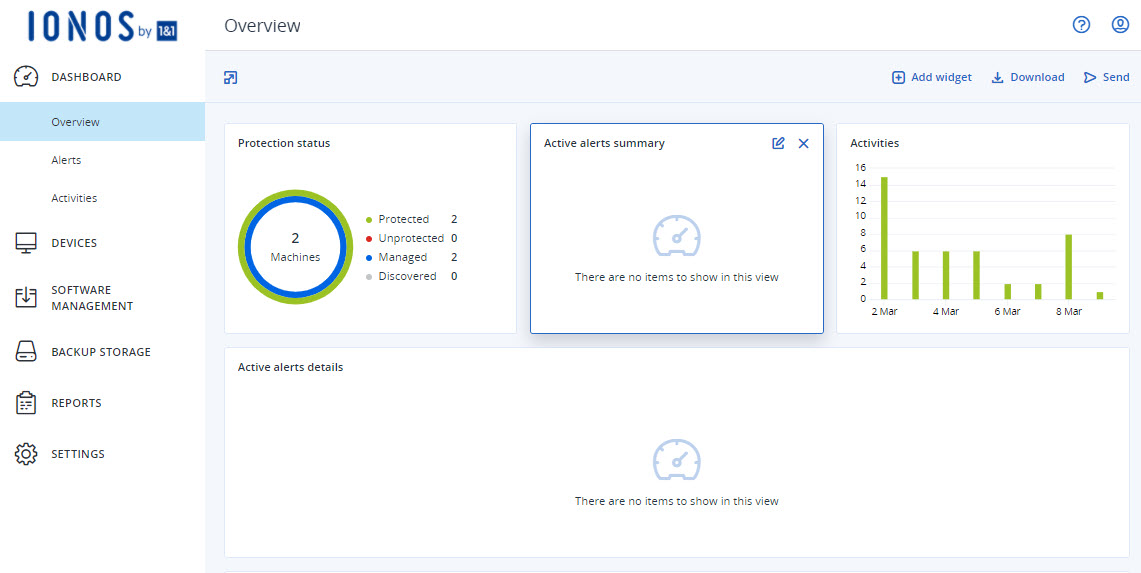
You can easily and conveniently manage your backups in the Backup Console. You can access this in the Cloud Panel in the Backup > Backup Package section. The Cloud Panel is an intuitive cloud-based interface where you can customise the storage space of your backup package. In addition, this area allows you to choose whether you want your device backups to be stored in data centres in Europe or the United States.
For each backup destination, there is a separate backup console where you can manage the devices you want to back up, your backup plans, and the backups you have already created. You can open these backup consoles from the Cloud Panel interface. For more information, click here:

Downloading Cyber Protection Agent and the Acronis Cyber Protect App
To create backups of your existing servers, you need to install the Acronis Cyber Protection Agent on these devices. You can download it from the Backup Console. If you ordered Cloud Backup with a server, the agent is preinstalled for most server operating systems.
If you want to back up smartphones or tablets with the Android operating system, or back up iPhones or iPads, you need to install the Acronis Cyber Protect app on these devices.
For instructions on installing the Acronis Cyber Protection Agent and the Acronis Cyber Protect app, click here:
Installing and setting up the Acronis Cyber Protect app (Android)
Install and set up the Acronis Cyber Protect App (iOS)
Install Backup Agent
Developing a Backup Strategy and Creating a Protection Plan
To restore your data quickly, efficiently, and completely, you should develop a backup strategy. When developing the appropriate backup strategy, you should consider various factors. These can have varying importance depending on the application scenario. For servers in particular, for example, you should check the legal requirements. How to develop an individual backup strategy is explained in the following article:
Protecting data and end devices with an effective backup strategy
To protect your servers, computers, and virtual machines, you need to configure a protection plan in the Backup Console. This protection plan is required to ensure that regular backups are made.
You can find an explanation of how to configure a new protection plan in the following article:


Protecting Computers and Servers from Viruses and Ransomware
With the Antivirus & Antimalware Protection module, you can secure Windows and Mac computers against malware threats, including cryptomining malware. Additionally, it offers a device control module that allows you to detect and prevent unauthorised access to and transmission of data over local data channels on computers. For this purpose, you can define access to device types and interfaces in this module and prevent certain actions. You can also define exceptions using positive lists for device types and USB devices.
The Vulnerability Assessment module allows you to scan computers and virtual machines running Microsoft Windows and Linux (CentOS 7/Virtuozzo/Acronis Cyber Infrastucture) operating systems for vulnerabilities. This way you can ensure that all installed applications and the operating systems used are up to date and working correctly.
These modules are enabled by default when you create a protection plan and can be customised by you at any time.
Managing Backups with the Backup Console
You can use the Backup Console to perform the following actions:
Add or delete workstations, servers, mobile devices, virtualization hosts, or applications
Create, edit, or delete backup schedules
Manage backups
Create scripting plans to automate regular actions on Windows and macOS machines in your environment
Perform anti-malware scans of backups
Replicate backups
Validate backups
Search and delete backups
Restore backups
Convert drive backups to a virtual machine
To create backups, you must then select an existing protection plan or create a new protection plan in the Backup Console.
The following article explains how to develop a custom backup strategy and select an existing protection plan in Backup Console:
Protect data and endpoints with an appropriate backup strategy
The following article explains how to configure a new protection plan:

Restoring Backups
For instructions on how to restore backups from computers running Microsoft Windows and macOS operating systems, see the following articles:
Restore backups on an iPhone or iPad
Restore backups on an Android mobile device
Additional Backup and Recovery Articles
