How to use PGP encryption for email
Businesses that use email as their main communication channel need to make sure that the information contained within their mails is secure. With PGP encryption, you can enhance the security of your email correspondence.
What is PGP encryption and how does it work?
PGP encryption offers an excellent means of protecting information and encrypting your emails. PGP (pretty good privacy) was originally developed in 1991 by Phil Zimmermann as a software program for encrypting emails. Over the years, PGP has established itself as the name for this encryption method.
PGP encryption is based on a public key protocol, where a key pair (a public and a private key) is used to encrypt and decrypt messages. The public key is available to potential email contacts and is directly transferred or uploaded on an external key server. This key enables your contacts to encrypt the emails that they send to you. Only you have access to the private key, which is normally protected with a password. It allows you to decrypt emails that are addressed to you and have been encrypted with a public key.
The person you’re communicating with should also be using PGP. This way they can provide you with access to their public key, allowing for secure incoming and outgoing emails from both parties. The public key protocol is described as an asymmetrical procedure since the two parties involved use different keys.
Securing your emails with PGP might seem like a lot of effort at first glance, but there are plugins that you can use to make the process of PGP encryption easier. Two of these types of plugins are FlowCrypt and Mailvelope. Many major email providers also provide their own PGP plugins that come with setup assistants.
What can PGP encryption be used for?
Asymmetric encryption like PGP has been used in the world of IT for quite some time. Below are some of the most popular use cases.
- Encrypting confidential messages: encrypting emails and other types of messages is one of the main ways that PGP is used.
- Encrypting files and file systems: in addition to encrypting messages, PGP can also be used to encrypt files that are stored on local storage devices or on a server.
- Digital signatures: PGP is also often used to check the authenticity of a message or file. With a PGP signature, you can determine whether a message is really from the person who sent it. Additionally, you can also see if it has been intercepted and possibly changed while being sent. PGP signatures can also be used to verify the authenticity of files (for example, programs).
How to set up PGP encryption
Many email clients now come with a PGP encryption package that includes setup instructions that are easy to follow. If, however, your email service provider hasn’t included instructions for setting up PGP, you can follow the steps below. The following PGP tutorial is a general approach to setting up PGP encryption.
PGP encryption with software
Step 1: select and install the appropriate PGP software
First, you need to find PGP software that is compatible with both your operating system and your email client. The open-source solution GnuPG (GNU Privacy Guard), which was released in 1997, is a great option for Linux users. The older 1.4 version comes pre-installed on many systems. The latest version, however, can be downloaded from the official website of GnuPG. Users of Windows or OS X operating systems can also find binary files on the GnuPG website. These files can be used to install the system-specific Gpg4win and MAC GPG, which are based on GnuPG.
Step 2: generate a key pair
Once the PGP program is installed, a key pair can be created. For Linux, open the command line and use the key generation command provided in the program’s manual. This example is for GnuPG:
sudo gpg --gen-keyThen select the type of encryption you want to use. You should only change it from the default setting (RSA and RSA) if you have sufficient knowledge of different encryption types and how they work.
Now, enter the key length in bits. The higher the value, the more secure the keys. A higher value, however, also results in slower performance. Security experts recommend a length of 4096 bits for RSA keys.
Next, enter the validity period of the keys and the name and email address that the key pair should be applied to. Finally, you need to confirm that the information you have provided is correct and select a passphrase for your private key. You will need this password later in order to decrypt your emails.
If you’re using Windows and mac OS X, you’ll start the process for generating keys with GUIs. Regardless of which PGP software and platform you are using, in most cases, you’ll be prompted to use random keyboard entries or mouse movements to generate the key.
Step 3: share the public key with your contacts
You can manage the generated keys under Linux either via the terminal or with Seahorse (for Gnome/Unity) or the graphical interface KGpg (for KDE). The command-line command for the private key using GnuPG is:
sudo gpg --list-secret-keys
sudo -Kand for the public key:
sudo gpg --list-keys
sudo -KIn addition to being able to see a list of the keys, you can also directly export them. The .asc file that is created can be sent as an attachment to your contacts via email or uploaded to a certificate server. If a contact has received your public key and has a key management program, they can send you encrypted messages. To send encrypted emails to the same contact , you’ll need their public key.
Online PGP encryption
Instead of using programs that you install on your own system, you can also use online PGP tools to create key pairs, encrypt your emails or decrypt emails you receive. Below we’ll take a look at the web service PGP Key Generator.
PGP Key Generator is a JavaScript program that enables key pair generation and can be executed in most web browsers. You can use the open-source service free of charge and without needing to register.
First, enter the required specifications for the keys in the Options form. Then click on Generate keys to start the key generation process. When the process is complete, you will be able to view the public key and your private key.
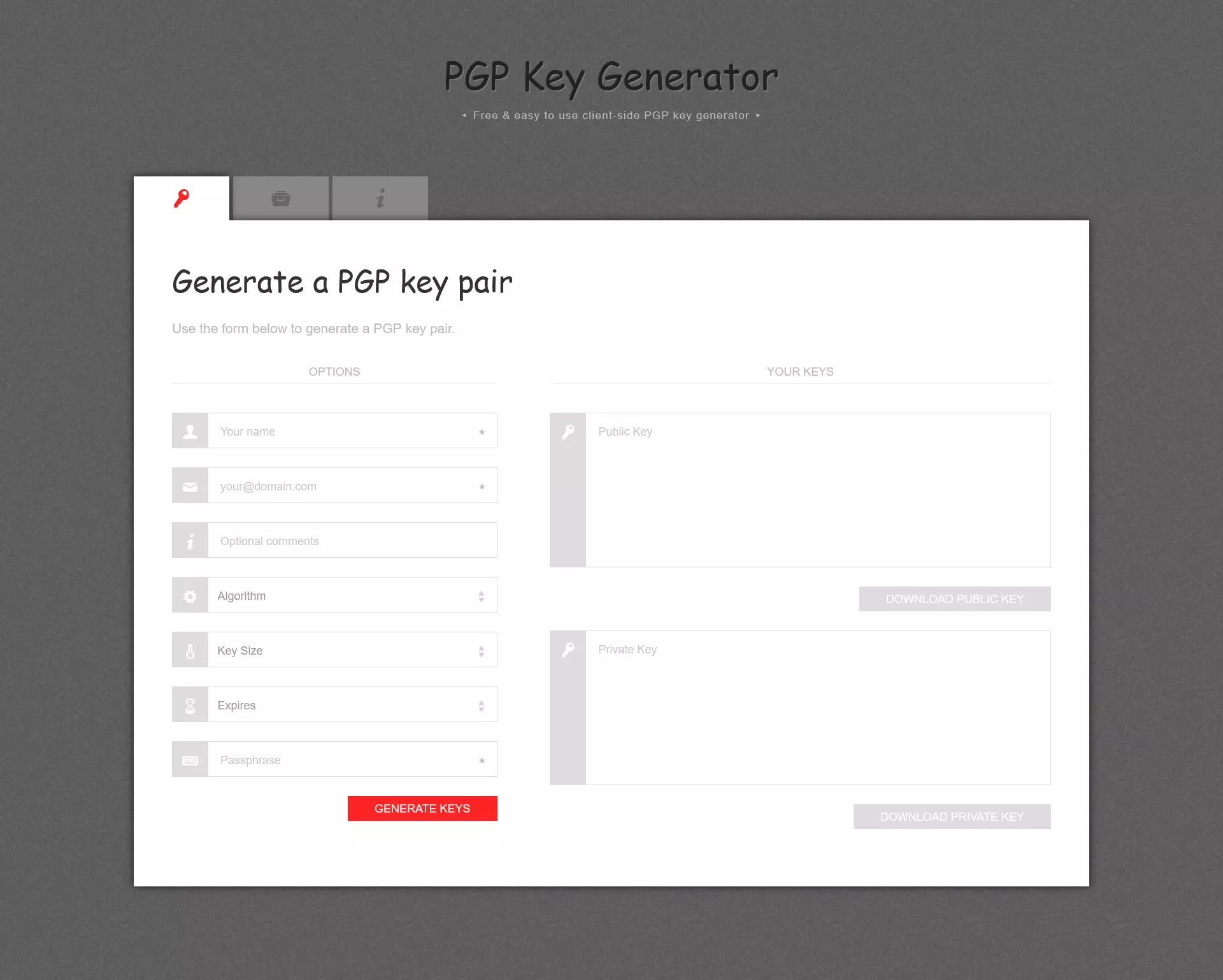
Since this web service is open source, experts can view the source code at any time. This means that they can continuously evaluate how secure and reliable the generator is. However, being a JavaScript application, there is also room for concern about cybercrime. If criminals are able to identify security gaps in the web service, these gaps can be exploited to attack your system and obtain sensitive information.
PGP encryption for email clients
If you prefer to communicate via email providers such as Gmail, Yahoo and Outlook, the browser extension Mailvelope is a good option for PGP encryption. The add-on is based on OpenPGP.js (a JavaScript implementation of the OpenPGP standard) and is available for Google Chrome, Microsoft Edge and Mozilla Firefox.
Once you have installed the extension, your browser’s toolbar will display the Mailvelope icon. You can use the icon to access the user interface, where you can create, import and manage your own keys as well as the public keys of your business partners. It’s also possible to upload public keys to a public key server.
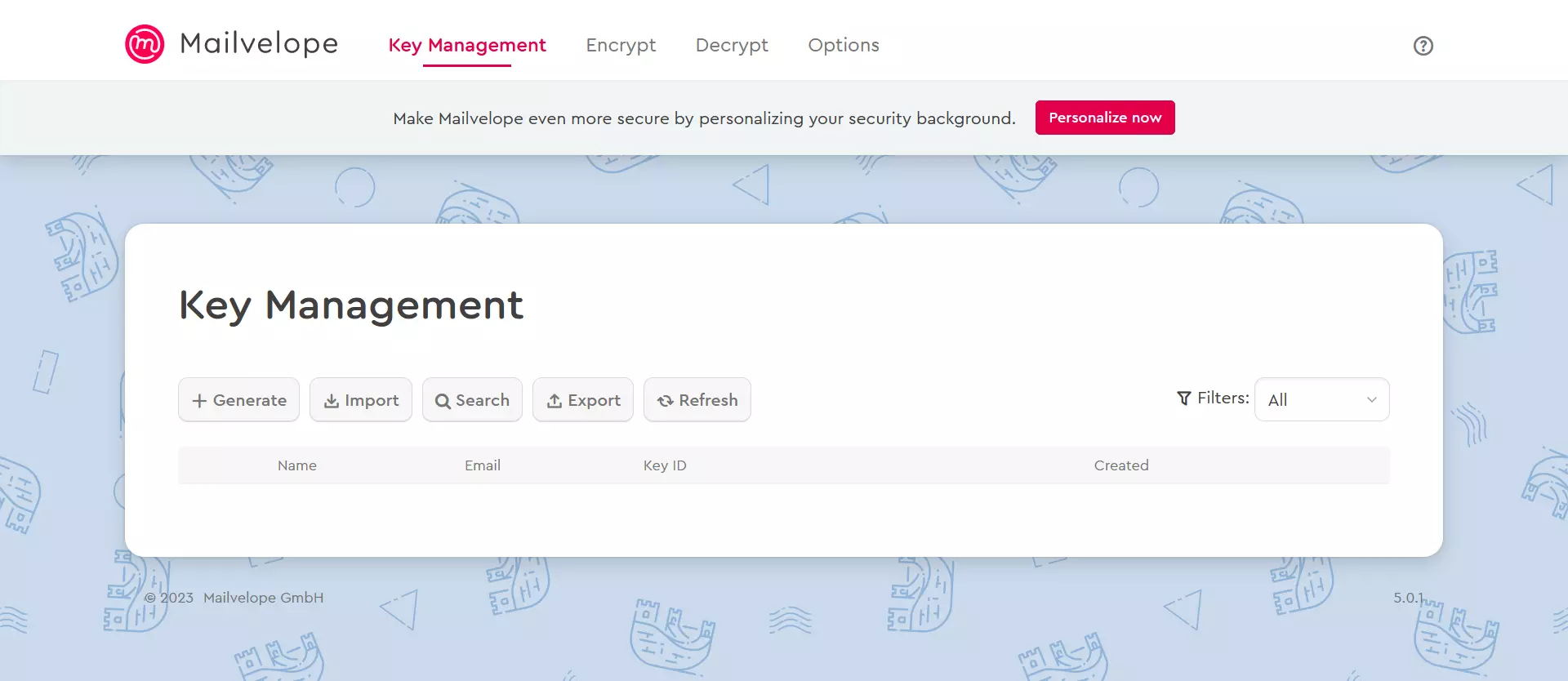
Once you’ve installed Mailvelope, the add-on will automatically scan for PGP messages when you access your account via your browser. The scanning process locates and displays specific elements for the encryption and decryption of PGP emails. In Options, you can enable or disable PGP encryption for Gmail, Outlook and other email providers.
- Write perfect emails with optional AI features
- Includes domain, spam filter and email forwarding
- Best of all, it's ad-free
PGP encryption on mobile devices
To use PGP encryption on iOS and Android devices, you need an email client that supports key management software and PGP encryption. Below we’ll look at two apps (one for each operating system) that you can use to save and manage the PGP keys of your contacts.
PGPro (iOS)
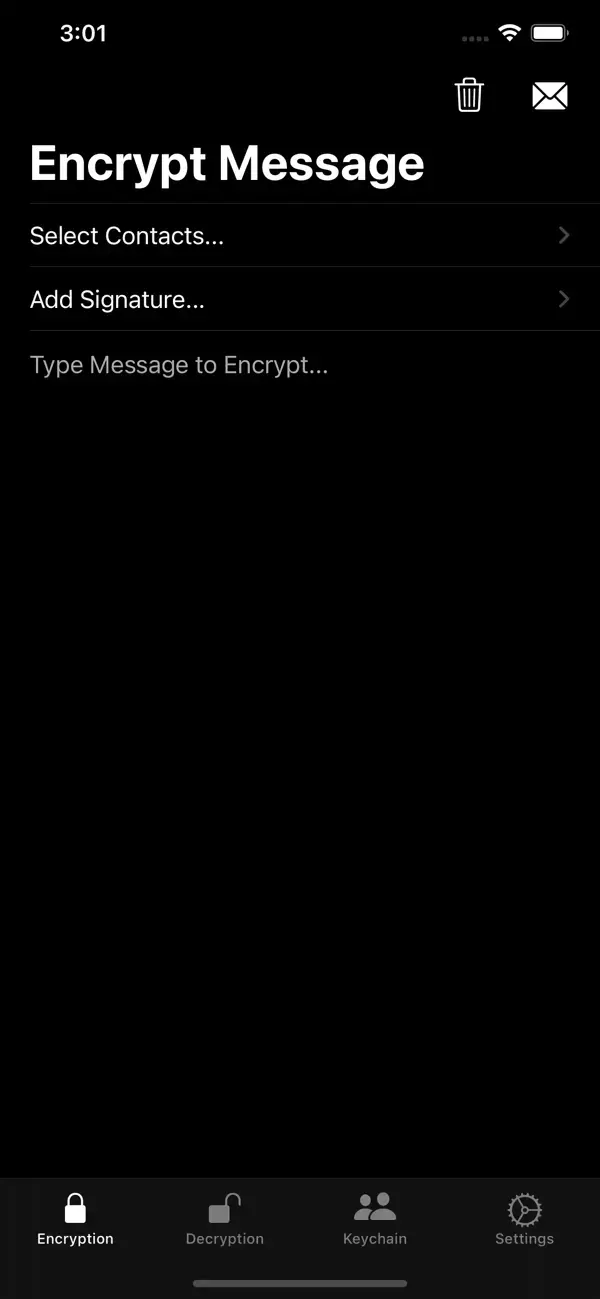
PGPro is an iOS app that can be used to create, manage and export PGP keys. The app is open source and based on the OpenPGP standard. With this app, all messages and keys are stored on your local device.
After you have installed the app from the App Store, you can generate or import new PGP key pairs under the tabKeychain. Under Encryption, you can use a public key to encrypt messages and under Decryption, you can use a private key to decrypt messages.
OpenKeychain (Android)
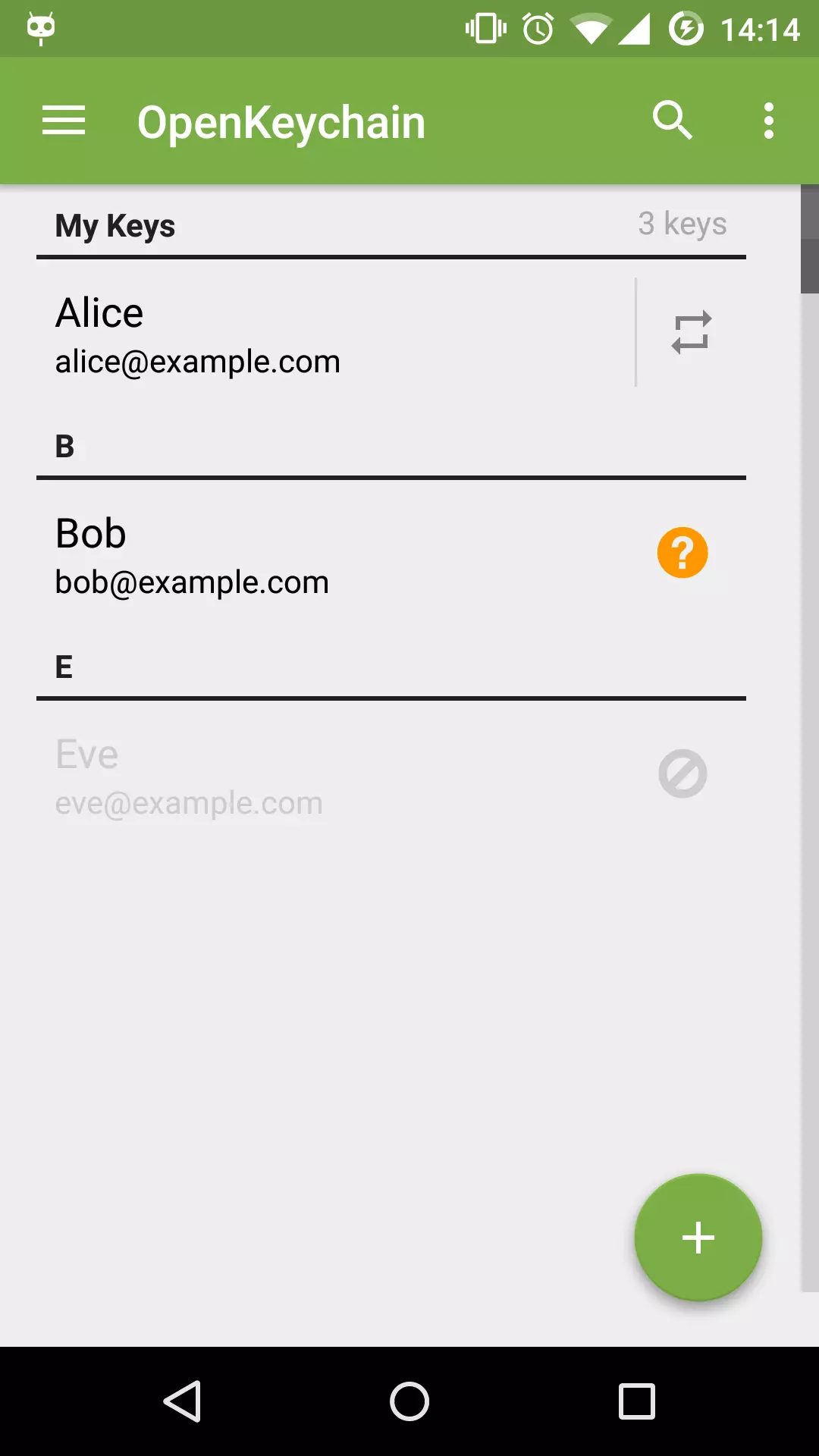
OpenKeychain is a great choice for Android users. This open-source app is also based on the Open PGP standard.
Once you have installed the app, you can navigate to the Keys section to view, import and manage all of your keys. Go to Encrypt/Decrypt to encrypt or decrypt messages and files.
Encrypted messages vs encrypted connections
Many users believe that SSL/TLS certificates are sufficient for email encryption. However, with these certificates only the transmission path of the email is encrypted. This means that messages can be intercepted by third parties and read in plain text.
Although they only encrypt the transmission path, SSL/TSL certificates allow for the encryption of elements that aren’t encrypted with PGP. These elements include information about the sender, recipient and the subject. Using a combination of PGP encryption and SSL/TSL encryption is the optimal solution for protecting the contents of your emails. Further information about encrypted transmission can be found in our Digital Guide article about encrypting emails with SSL/TLS.
- Secures data transfers
- Avoids browser warnings
- Improves your Google ranking