LDAP (Lightweight Directory Access Protocol)
LDAP was developed as an application and access protocol for directory service providers. The LDAP protocol can be used to search, modify, or authenticate data, information, and items on a large scale in distributed directory services and to manage communications with directory databases.
- Free website protection with SSL Wildcard included
- Free private registration for greater privacy
- Free 2 GB email account
LDAP Protocol: Definition
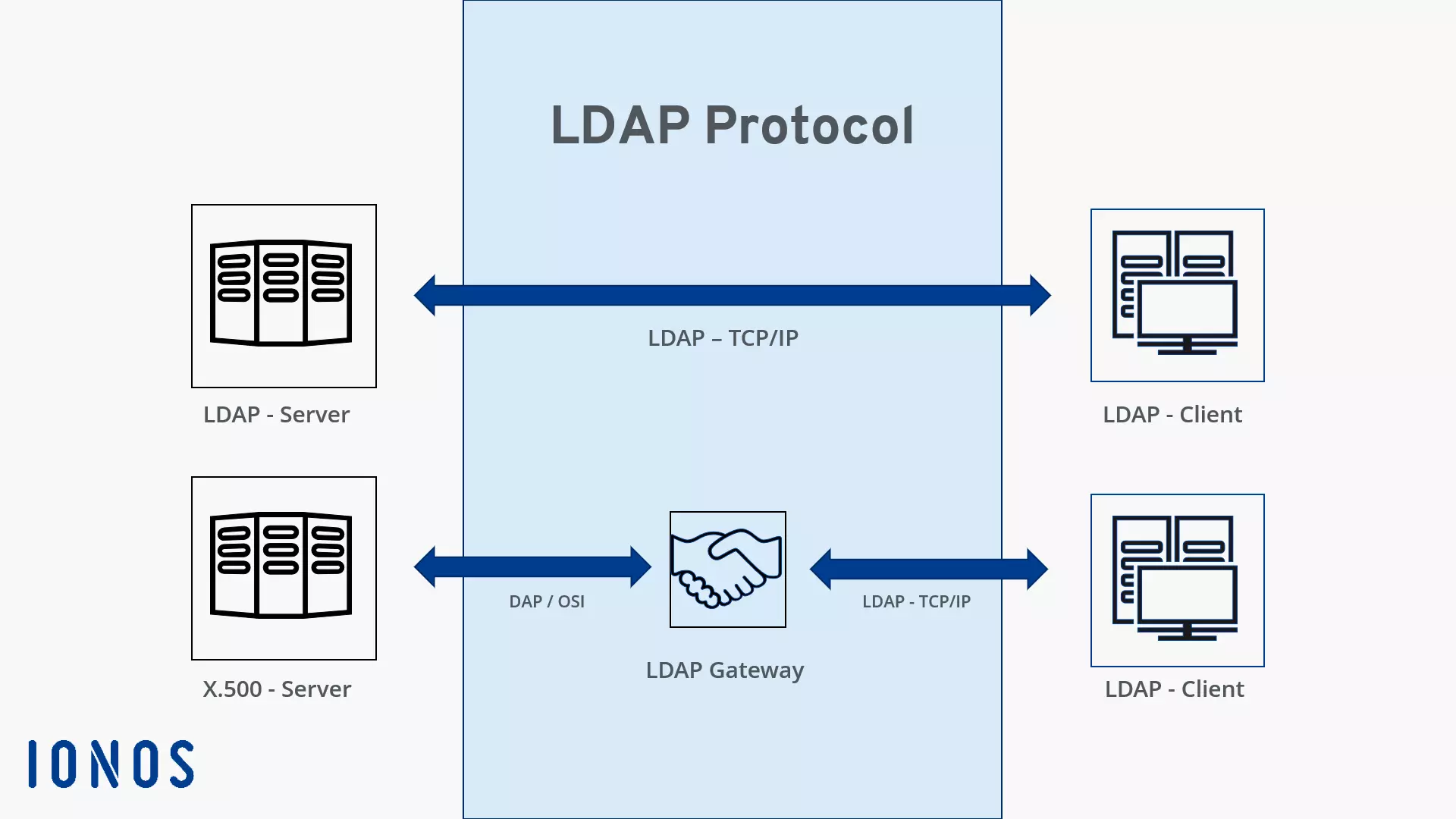
LDAP, written out ‘Lightweight Directory Access Protocol’, belongs to the group of network protocols and is used as a standardised access protocol for queries and changes according to the client-server model in distributed, central directory services. In this context, the term LDAP server is often used when directory servers communicate via the LDAP protocol. The ‘lightweight’ comes from the fact that it is considered a lightweight variant of the DAP access protocol (Directory Access Protocol) specified according to X.500. Since DAP is too complex for effective implementation in large enterprises with extensive user data, LDAP is often used in practice.
LDAP is based on a TCP/IP protocol stack and can be used flexibly for any directory system. For the transport of data, it can use TCP and UDP ports. It is particularly common in areas and industries that need to process and manage large amounts of data and information, such as telecommunications, aviation, IT, and hardware and software development. Standard ports for data transfers are port 389 for unsecured data transfers and port 636 for TLS encrypted data transfers.
How does LDAP work?
To understand how LDAP works, it is important to understand the role it plays in LDAP directory services. With increasing digitalisation, companies rely on processing and organising data efficiently. To structure them clearly and to query or change them without a big effort, directory services are used. In these, information and attributes for various objects such as users, hardware, applications, workstations or login data are organised in a hierarchical tree structure called DIT (Directory Information Tree).
LDAP is used as a means of communication for LDAP directories and LDAP servers to efficiently search, modify, or authenticate attributes in a complex directory service. LDAP clients access the relevant directory via the LDAP server or an LDAP gateway. An LDAP server is usually a directory server whose data structure complies with the LDAP specifications, and which performs data transfers using the current LDAP protocol version 3 (as of February 2022).
LDAP uses at a glance
Important and common tasks and uses of LDAP include:
- Central storage/authentication/authorisation of user data and passwords.
- Inserting entries and operations into the directory database
- Authenticate or bind sessions
- Modify, search, compare, extend, or delete directory entries
- Searching schemas
- Submitting queries
- Unbinding operations
Building LDAP directories
LDAP configurations use a standardised hierarchical tree structure (DIT) for directories and data structure, which can be distributed over many servers. The standardisation is done by the respective schema of object classes and their attributes. The tree hierarchy, in turn, breaks down or branches out into various representative political, geographic, or organisational levels as follows:
- Root (root)
- Countries
- Organisations
- Organisational units
- People
- Individuals / resources
The LDAP directory can exist on LDAP servers as a replicated complete version that synchronises changes to the original. Queries to the directory run through LDAP servers, also called Directory System Agents (DSA), which can distribute queries to additional DSA servers, but guarantee users a fast, efficiently abstracted response.
LDAP uses an object-orientated programming approach, which includes objects, classes, inheritance, and associated polymorphism. An independent LDAP directory entry (LDAP object) is composed of attributes and the mandatory object name ‘Distinguished Name’. The structure of the Distinguished Name is similar to file naming conventions and prevents identical objects on one level. Attributes that make up an object each have a specific type, identified by abbreviations such as cn (common name), st (state), or sn (surname). In addition, attributes can be single- or multi-valued, depending on the type. While there are container objects that contain objects, the ends of a tree hierarchy branch into individual leaf objects.
The protocol uses specific access sequences that tell the LDAP server who is accessing the directory via the bind directive and a distinguished name (DN). BaseDN can be used to define which directory levels are eligible for search, using specifications such as base (this object), sub (this and all objects below it), or one (the level below the baseDN). Search queries are usually not performed manually by end users, but via LDAP-enabled programs (e.g. Outlook). In turn, the respective directory service controls who is allowed to access.
Relationship between LDAP and Active Directory
LDAP, along with Kerberos, SMB and DNS, is one of the four central standard protocols that provide seamless communication and data transfers in Microsoft’s Active Directory. Active Directory is designed to be used as a directory service in Exchange Servers with LDAP support to provide unified queries to Active Directory directories and to integrate LDAP-based services into the AD environment.
Active Directory is a powerful, relatively scalable directory service for large enterprises with several thousand employees and focuses on Windows structures. The LDAP Protocol, on the other hand, offers more flexibility and extensibility for large deployments with branched user communities due to its Linux/Unix environment and open source compatibility. For this reason, LDAP and LDAP servers are also used in industries such as mobile communications and aviation, where several million user authentication requests are processed.
Use cases of the LDAP protocol
Use cases in which the use of LDAP is worthwhile include:
- User and system administration
- Mapping of protocols and RFCs
- NIS information/boot information
- Administration of DNS zone data and mountpoints
- Organisation of aliases (email) and DHCP servers
LDAP is particularly prevalent in areas that rely on comprehensive address queries and user authentication. These include:
- Address books: Management software solutions for digital contact/address books such as Mozilla Thunderbird, Microsoft Outlook, or Apple Contacts.
- User management: Directory services for user management such as Apple Open Directory, Microsoft Active Directory, or NetlQ eDirectory.
- Authentication: Programming interfaces for user authentication such as PAM.
- User data management: Organisation/management of user data in POP/IMAP/SMTP servers or in database systems and mail servers such as qmail, sendmail, or exim.
- Document management systems: Legitimisation of requesting users or generation of telephone directories as in multifunction printers, AntiSpam solutions, VoIP, WebProxy, or NetScaler.
LDAP: Advantages at a glance
LDAP enables optimised authentication, authorisation, and an efficient search for address and user data. Because of its many benefits for enterprises, LDAP serves as an industry standard that most software products support. The main advantages are fast queries and connections, a lean query language, and the clearly structured protocol. Access to data and its readout in LDAP-enabled directory services is fast thanks to non-normalised data storage. This is particularly noticeable in areas with many small, not strongly subdivided data entries.
LDAP also offers a lot of time savings and powerful data structures for regular queries in large data sets or for distributed data storage, including server-wide distributed directory services, coupled directory replication for data reconciliation, and reliable high availability. The SSL/TLS-secured LDAP variant LDAPS also guarantees encryption of sender and recipient data and therefore certificate-based authentication. By establishing an SSL/TLS connection, the data exchange is additionally protected against manipulation and data theft.
- Write perfect emails with optional AI features
- Includes domain, spam filter and email forwarding
- Best of all, it's ad-free